In today’s technologically driven world, seamless IT operations are paramount for businesses of all sizes. IT support services are no longer a luxury but a critical component of operational efficiency and success. This guide delves into the multifaceted world of IT support, exploring its core functions, delivery models, essential technologies, and the crucial role it plays in maintaining business continuity and cybersecurity.
From understanding the different tiers of support and the key performance indicators that measure their effectiveness, to navigating the complexities of service level agreements and the ever-evolving landscape of cybersecurity threats, this comprehensive overview aims to provide a clear and insightful understanding of the vital role IT support plays in the modern business environment.
Defining IT Support Services
IT support services encompass the various technical assistance and maintenance activities that ensure the smooth and efficient operation of an organization’s information technology infrastructure. These services are crucial for maintaining productivity, safeguarding data, and enabling the seamless use of technology by employees and customers. Effective IT support minimizes downtime, resolves technical issues promptly, and proactively prevents future problems.The core functions of IT support services revolve around providing technical assistance, troubleshooting problems, and maintaining the organization’s IT infrastructure.
This includes everything from setting up new computers and software to resolving complex network issues and ensuring data security. They act as a bridge between the technical complexities of IT and the end-users who rely on it daily.
Types of IT Support Services
Different organizations require varying levels of IT support, leading to the development of specialized service models. The type of service best suited to an organization depends on factors like size, industry, and the complexity of its IT infrastructure.
- Help Desk Support: This is the first point of contact for most users experiencing IT issues. Help desk technicians handle common problems, such as password resets, software troubleshooting, and basic hardware issues. They often use a ticketing system to track and manage requests.
- Field Service Support: This involves on-site visits to resolve IT problems that cannot be addressed remotely. Field technicians are typically equipped with tools and expertise to diagnose and repair hardware issues, install equipment, and provide in-person training.
- Remote Support: Leveraging technology such as remote desktop software, remote support allows technicians to access and troubleshoot user devices remotely. This is a cost-effective and efficient way to resolve many IT issues without requiring an on-site visit.
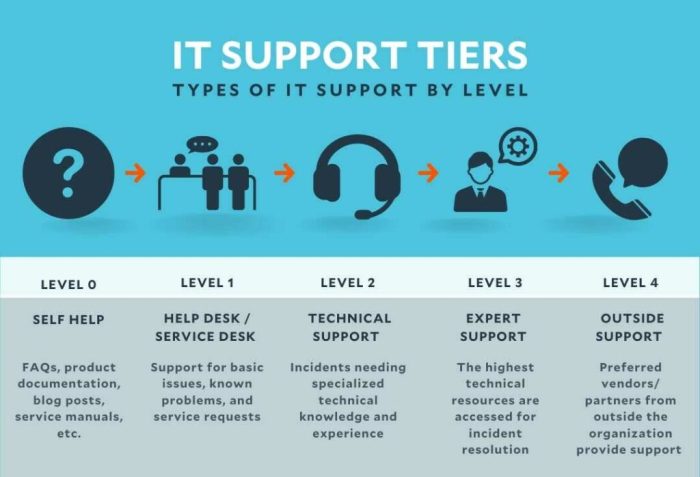
Levels of IT Support
Many organizations structure their IT support teams into tiered levels, each with increasing expertise and responsibility. This tiered approach ensures that issues are addressed efficiently and escalated appropriately when necessary.
- Tier 1 Support: This level handles basic troubleshooting and common issues. Tier 1 technicians typically have a broad understanding of various IT systems and use established procedures to resolve routine problems. They often act as the first line of defense, directing more complex issues to higher tiers.
- Tier 2 Support: Tier 2 technicians possess more specialized knowledge and skills than Tier 1. They handle more complex issues that require deeper technical expertise. They may investigate the root cause of problems and implement solutions that require a more in-depth understanding of IT systems.
- Tier 3 Support: This is the highest level of support, reserved for the most complex and critical issues. Tier 3 technicians are highly specialized and possess advanced troubleshooting skills. They often deal with system failures, network outages, and security breaches, requiring deep technical knowledge and experience.
Key Performance Indicators (KPIs) for IT Support Services
Measuring the effectiveness of IT support services is crucial for continuous improvement and demonstrating value to the organization. KPIs provide quantifiable metrics to track performance and identify areas for enhancement.
- Mean Time To Resolution (MTTR): This metric measures the average time it takes to resolve an IT issue. A lower MTTR indicates more efficient support processes.
- First Call Resolution (FCR): This measures the percentage of issues resolved on the first contact. Higher FCR rates demonstrate effective problem-solving and efficient knowledge transfer.
- Customer Satisfaction (CSAT): This measures the level of satisfaction users have with the IT support services. CSAT scores are often collected through surveys or feedback forms.
- Ticket Volume: The total number of support tickets received over a given period provides insights into the demand for IT support and potential areas for improvement in proactive support.
IT Support Service Delivery Models
Choosing the right IT support delivery model is crucial for a business’s operational efficiency and overall success. The model selected significantly impacts cost, responsiveness, and the level of control a company maintains over its IT infrastructure. This section will explore the various models available, highlighting their strengths and weaknesses.
In-House IT Support
In-house IT support involves employing a dedicated team of IT professionals within the organization. This team is responsible for managing all aspects of the company’s IT infrastructure, from network maintenance to software support. The advantages include greater control over IT operations, potentially faster response times to internal issues, and a deeper understanding of the company’s specific needs. However, disadvantages include higher upfront and ongoing costs associated with salaries, benefits, training, and equipment.
Maintaining a skilled in-house team can also be challenging, particularly in rapidly evolving technological landscapes. Smaller companies may find the financial burden of maintaining a full in-house team prohibitive.
Outsourced IT Support
Outsourcing IT support involves contracting with a third-party provider to manage some or all of a company’s IT needs. This can range from help desk support to full-scale managed services. The benefits include cost savings compared to in-house teams, access to specialized expertise and resources that may not be readily available internally, and the ability to scale IT support up or down as needed.
Potential drawbacks include less direct control over IT operations, potential communication challenges, and dependency on the responsiveness and reliability of the external provider. Security concerns and potential data breaches are also valid considerations when choosing this model.
Hybrid IT Support
A hybrid model combines elements of both in-house and outsourced support. This approach allows companies to leverage the strengths of both models while mitigating their weaknesses. For instance, a company might maintain a small internal IT team for critical tasks and strategic projects, while outsourcing routine maintenance and help desk functions to a third-party provider. This balance offers a flexible and potentially cost-effective solution.
However, successful implementation requires careful planning and coordination between internal and external teams. Clear responsibilities and communication protocols are essential to prevent conflicts and ensure seamless service delivery.
Hypothetical IT Support Service Delivery Model for a Small Business
For a small business with a limited budget and staff, a hybrid model incorporating a combination of managed services and a part-time internal IT specialist might be ideal. The managed service provider could handle routine tasks like help desk support, network monitoring, and basic security, while a part-time internal specialist could focus on strategic projects, internal system administration, and specialized support requests requiring a deep understanding of the company’s specific processes.
This allows for cost-effectiveness without sacrificing the responsiveness and specialized expertise necessary for smooth operations.
Elements of a Service Level Agreement (SLA) for IT Support Services
A well-defined SLA is critical for successful IT support. It Artikels the expectations and responsibilities of both the provider and the client. Key elements include:
- Service Scope: A clear definition of the services covered by the agreement.
- Service Level Targets: Specific, measurable targets for key performance indicators (KPIs), such as response times, resolution times, and system uptime.
- Reporting and Monitoring: Procedures for monitoring service performance and generating regular reports.
- Escalation Procedures: A defined process for handling issues that cannot be resolved within agreed-upon timeframes.
- Service Credits or Penalties: Mechanisms for compensating the client in case of service failures.
- Communication Protocols: Clear guidelines for communication between the provider and the client.
- Termination Clause: Conditions under which the agreement can be terminated.
A well-structured SLA ensures transparency and accountability, promoting a positive and productive relationship between the IT support provider and the client.
Technologies Used in IT Support
Effective IT support relies heavily on a robust suite of software and hardware tools, enabling technicians to diagnose, troubleshoot, and resolve technical issues efficiently. The right tools empower support teams to provide timely and effective assistance, minimizing downtime and improving user satisfaction. This section explores the key technologies employed in modern IT support environments.
Essential Software and Hardware Tools
Providing comprehensive IT support requires a combination of software and hardware. Essential software includes operating system diagnostic tools (like Windows System Information or macOS System Report), remote access software (discussed in detail below), ticketing systems for managing support requests, and monitoring tools for proactive maintenance. Hardware tools commonly used include laptops or desktops with sufficient processing power and memory, network diagnostic equipment (such as network cables and testers), and external storage devices for backups and data transfers.
Specialized hardware, such as server racks or data center equipment, might also be necessary depending on the scale and complexity of the IT infrastructure being supported.
Remote Access Tools and Their Efficiency
Remote access tools are indispensable for modern IT support, allowing technicians to connect to and control end-users’ devices remotely. This eliminates the need for on-site visits in many cases, significantly reducing response times and improving efficiency. Tools like TeamViewer, AnyDesk, and LogMeIn Pro provide secure connections, enabling technicians to troubleshoot problems, install software, and perform other tasks as if they were physically present at the user’s location.
The ability to see the user’s screen in real-time facilitates faster problem resolution and allows for collaborative troubleshooting. Moreover, remote access reduces travel costs and time, making support more cost-effective and scalable.
Ticketing Systems and Their Functionalities
Ticketing systems are crucial for organizing and managing IT support requests. These systems provide a centralized platform for users to submit requests, track their progress, and receive updates. Popular examples include Zendesk, Jira Service Management, and Freshdesk. These systems typically offer features such as automated routing of tickets based on priority or subject, customizable workflows for managing requests, and reporting tools to track key metrics like resolution times and customer satisfaction.
The ability to assign tickets to specific technicians, add notes and updates, and generate reports ensures a structured and efficient approach to managing support requests, improving both technician productivity and user experience.
Comparison of Remote Monitoring and Management (RMM) Tools
Remote Monitoring and Management (RMM) tools provide proactive monitoring and automated management capabilities, allowing IT support teams to identify and address potential issues before they impact users. Several RMM tools exist, each with its strengths and weaknesses. The following table compares some popular options:
| RMM Tool | Key Features | Pricing Model | Strengths |
|---|---|---|---|
| Datto RMM | Remote control, patch management, automated backups, security monitoring | Subscription-based | Comprehensive features, robust security, strong reporting |
| ConnectWise Manage | Ticketing, project management, time tracking, RMM capabilities | Subscription-based | Integrated PSA and RMM functionality, extensive automation |
| NinjaOne | Remote control, patch management, endpoint detection and response (EDR), IT automation | Subscription-based | Ease of use, strong automation capabilities, affordable pricing options |
| SolarWinds N-central | Remote control, network monitoring, automated remediation, reporting and analytics | Subscription-based | Comprehensive monitoring and management capabilities, robust reporting |
IT Support and Cybersecurity

IT support plays a crucial role in maintaining a company’s cybersecurity posture. A robust IT support team acts as the first line of defense against cyber threats, implementing and maintaining security measures, responding to incidents, and educating users on safe practices. Their expertise ensures the organization’s digital assets and sensitive data remain protected.
The Role of IT Support in Maintaining Cybersecurity
IT support’s contribution to cybersecurity extends beyond basic troubleshooting. They are responsible for implementing and maintaining security software, such as antivirus and firewalls, ensuring these systems are up-to-date and configured correctly. They also manage user access controls, regularly reviewing permissions and identifying potential vulnerabilities. Furthermore, IT support handles incident response, investigating security breaches, containing the damage, and implementing remediation strategies.
Proactive monitoring of network traffic and systems for suspicious activity is another key responsibility. Regular security audits and vulnerability assessments are also conducted by, or in close collaboration with, IT support teams.
Common Cybersecurity Threats and Vulnerabilities
Organizations face a multitude of cybersecurity threats. Phishing attacks, where malicious actors impersonate legitimate entities to steal sensitive information, remain a prevalent threat. Malware, encompassing viruses, ransomware, and spyware, can compromise systems and data integrity. Denial-of-service (DoS) attacks overwhelm systems, rendering them inaccessible. Insider threats, stemming from malicious or negligent employees, also pose a significant risk.
Vulnerabilities in software and hardware, often exploited through outdated systems or unpatched software, create entry points for attackers. Weak or easily guessable passwords significantly increase the risk of unauthorized access. Finally, social engineering tactics, which manipulate individuals into divulging confidential information, represent a constant and evolving challenge.
Best Practices for Preventing Security Breaches
Implementing a multi-layered security approach is paramount. This includes employing strong passwords and multi-factor authentication (MFA) to restrict access to systems. Regular software updates and patching are essential to mitigate known vulnerabilities. Robust security awareness training for employees is crucial to educate them about phishing attempts and other social engineering techniques. Implementing a strong firewall and intrusion detection/prevention systems (IDS/IPS) helps to monitor and block malicious network traffic.
Regular security audits and penetration testing identify weaknesses in the security infrastructure before attackers can exploit them. Data backups and disaster recovery planning ensure business continuity in the event of a security incident. Finally, adhering to data privacy regulations, such as GDPR or CCPA, is vital for protecting sensitive information.
Security Measures IT Support Should Implement
Implementing effective security measures is a continuous process requiring proactive monitoring and adaptation. Here are some key security measures IT support should implement:
- Regular Security Audits and Vulnerability Scans: Proactive identification and remediation of vulnerabilities.
- Firewall Management: Configuring and maintaining firewalls to control network traffic and block malicious activity.
- Intrusion Detection/Prevention Systems (IDS/IPS): Monitoring network traffic for suspicious activity and automatically blocking threats.
- Antivirus and Antimalware Software: Deploying and maintaining up-to-date antivirus and antimalware solutions across all systems.
- Data Backup and Disaster Recovery: Regularly backing up critical data and establishing a robust disaster recovery plan.
- Access Control Management: Implementing strong password policies, multi-factor authentication, and least privilege access controls.
- Security Awareness Training: Educating employees about cybersecurity threats and best practices.
- Incident Response Plan: Developing and regularly testing an incident response plan to handle security breaches effectively.
- Regular Software Updates and Patching: Keeping all software and operating systems up-to-date with the latest security patches.
- Email Security: Implementing email security measures such as spam filtering and anti-phishing solutions.
The Future of IT Support
The IT support landscape is undergoing a rapid transformation, driven by technological advancements and evolving business needs. The traditional model of reactive, on-site support is giving way to proactive, remote, and increasingly automated solutions. This shift necessitates a reevaluation of skills, strategies, and the overall approach to providing effective IT support.
Emerging trends like artificial intelligence (AI) and automation are fundamentally reshaping how IT support is delivered and consumed. Cloud computing is no longer a niche technology but a foundational element of modern IT infrastructure, impacting every aspect of support, from service delivery to security. Understanding these shifts is crucial for businesses and IT professionals alike to remain competitive and relevant in the evolving digital world.
Emerging Trends in IT Support
AI and automation are poised to revolutionize IT support. AI-powered chatbots and virtual assistants are already handling a significant portion of first-level support requests, providing immediate answers to common questions and resolving simple issues without human intervention. Automation tools are streamlining repetitive tasks, such as password resets and software updates, freeing up human technicians to focus on more complex problems.
For example, companies like IBM are heavily investing in AI-driven support systems that can diagnose and resolve issues autonomously, significantly reducing resolution times and improving overall efficiency. This allows human support staff to concentrate on more strategic tasks and complex troubleshooting.
The Impact of Cloud Computing on IT Support
The widespread adoption of cloud computing has profoundly altered the nature of IT support. With applications and data residing in the cloud, traditional on-site support becomes less relevant. Cloud-based support tools allow technicians to remotely monitor and manage systems, troubleshoot issues, and provide support regardless of geographical location. This shift towards remote support enhances scalability, flexibility, and cost-effectiveness.
For instance, a small business can leverage cloud-based support solutions to access enterprise-grade support capabilities without the significant investment in on-site infrastructure and personnel. The cloud also simplifies disaster recovery and business continuity planning, offering robust backup and recovery options that minimize downtime and data loss.
Predictions for the Future of IT Support Services
The future of IT support points towards a more proactive, predictive, and personalized approach. AI and machine learning will play a crucial role in predicting potential issues before they impact users, enabling proactive intervention and preventing disruptions. Augmented reality (AR) and virtual reality (VR) technologies are expected to enhance remote support capabilities, allowing technicians to remotely guide users through complex troubleshooting procedures with greater precision and efficiency.
We can anticipate a rise in specialized support services catering to specific industry needs and technological advancements, such as those focused on cybersecurity, IoT device management, and AI-driven systems. For example, the increased reliance on IoT devices in various sectors will create a surge in demand for specialized support services focusing on securing and maintaining these interconnected systems.
Skills Needed for IT Support Professionals in the Coming Years
The evolving IT support landscape demands a new set of skills for professionals in this field. Beyond technical expertise in traditional areas, professionals will need strong analytical and problem-solving skills to effectively utilize AI-powered tools and interpret data. Adaptability and continuous learning are essential to keep pace with rapid technological advancements. Strong communication and interpersonal skills remain crucial for effective interaction with users, regardless of the level of automation.
Furthermore, expertise in cloud technologies, cybersecurity, and data analytics will become increasingly important. For example, understanding cloud security protocols and best practices is no longer a luxury but a necessity for IT support professionals. The ability to analyze large datasets to identify trends and predict potential problems will also be highly valued.
IT SUPPORT (Specific Focus)

Proactive IT support is crucial for maintaining a smooth and efficient operational environment. It shifts the focus from reactive problem-solving to preventative measures, ultimately reducing downtime, improving productivity, and minimizing the overall cost of IT ownership. By anticipating potential issues and addressing them before they impact users, proactive support ensures a higher level of service availability and user satisfaction.Proactive IT support involves anticipating potential problems and taking steps to prevent them before they occur.
This approach contrasts with reactive support, which only addresses issues after they have already impacted users or systems. A proactive strategy leads to a more stable and reliable IT infrastructure, reducing the need for emergency interventions and associated disruptions.
Examples of Proactive IT Support Measures
Proactive measures are diverse and tailored to the specific needs of an organization. They encompass a range of activities, from routine system checks to advanced predictive analytics. Implementing a mix of these strategies creates a robust preventative approach.
- Regular System Backups: Implementing a robust backup and recovery system ensures data protection and allows for quick restoration in case of data loss or system failure. This includes testing the recovery process regularly to validate its effectiveness.
- Software Updates and Patching: Regularly applying security patches and software updates is critical to mitigating vulnerabilities and preventing security breaches. A well-defined update schedule, communicated to users, minimizes disruptions.
- Network Monitoring: Continuous monitoring of network performance, bandwidth usage, and potential bottlenecks allows for early detection of issues and proactive adjustments to maintain optimal network health. Real-time alerts can prevent performance degradation.
- Hardware Maintenance: Regular cleaning, inspection, and testing of hardware components prevent premature failure and extend their lifespan. This includes server maintenance, peripheral checks, and preventative replacements.
- Security Audits and Penetration Testing: Regular security assessments identify vulnerabilities in the IT infrastructure and allow for the implementation of necessary security measures to prevent breaches. Penetration testing simulates real-world attacks to identify weaknesses.
Benefits of Preventative Maintenance for IT Infrastructure
Preventative maintenance significantly reduces the risk of unexpected downtime and costly repairs. By addressing potential problems before they escalate, it ensures a more stable and reliable IT environment. The overall impact on productivity and user satisfaction is also greatly improved.
- Reduced Downtime: Preventative maintenance significantly minimizes unexpected outages, leading to increased operational efficiency and reduced loss of productivity.
- Lower Repair Costs: Addressing minor issues before they become major problems significantly reduces the overall cost of repairs and replacements.
- Improved System Performance: Regular maintenance optimizes system performance, leading to faster processing speeds and improved responsiveness.
- Enhanced Security: Proactive security measures, such as regular patching and security audits, strengthen the IT infrastructure against cyber threats.
- Increased Employee Productivity: A stable and reliable IT infrastructure allows employees to focus on their work without interruptions caused by technical issues.
Creating a Preventative Maintenance Schedule
A well-structured preventative maintenance schedule is essential for effective proactive IT support. The schedule should be tailored to the specific needs of the organization and should include regular checks, updates, and maintenance tasks.The process involves identifying all critical IT assets, determining their maintenance requirements, and scheduling regular maintenance activities. This schedule should be documented and communicated to the relevant IT personnel.
A clear schedule ensures that all necessary maintenance tasks are performed consistently and efficiently. For example, a sample schedule might include weekly backups, monthly software updates, quarterly hardware inspections, and annual security audits. The frequency of each task depends on the criticality of the asset and its potential impact on business operations. The schedule should be reviewed and updated regularly to reflect changes in the IT infrastructure or business needs.
Utilizing a ticketing system or dedicated maintenance management software can greatly assist in tracking and managing the schedule.
Ultimately, effective IT support services are the bedrock of a smoothly functioning organization. By understanding the various aspects explored in this guide—from proactive maintenance to robust cybersecurity measures—businesses can ensure their technology infrastructure remains resilient, secure, and optimally supports their operational goals. Investing in and strategically managing IT support translates directly to increased productivity, enhanced employee satisfaction, and a significant reduction in costly downtime.
FAQ Summary
What is the difference between Tier 1, Tier 2, and Tier 3 support?
Tier 1 handles basic troubleshooting, Tier 2 tackles more complex issues, and Tier 3 addresses advanced problems requiring specialized expertise.
How much should I budget for IT support services?
Budgeting depends on factors like business size, complexity of systems, and chosen service model (in-house vs. outsourced). A thorough needs assessment is crucial.
What is an SLA, and why is it important?
A Service Level Agreement (SLA) Artikels the agreed-upon service levels, response times, and other performance metrics between an IT support provider and a client, ensuring accountability and transparency.
What are some common signs I need to upgrade my IT infrastructure?
Slow performance, frequent crashes, outdated software, security vulnerabilities, and insufficient storage capacity are all indicators of a need for upgrades.






