
In today’s interconnected world, robust network security is paramount. From small businesses to global corporations, the threat landscape is constantly evolving, demanding proactive and adaptive security measures. This guide delves into the core components of effective network security, exploring various solutions, implementation strategies, and future trends. We will examine the critical role of IT support, the importance of employee training, and the ever-increasing need for advanced technologies to combat emerging threats.
Understanding network security isn’t just about deploying technology; it’s about establishing a comprehensive security posture that integrates people, processes, and technology. This guide aims to provide a clear and practical understanding of how to build and maintain a secure network environment, equipping readers with the knowledge to navigate the complexities of modern cybersecurity.
Defining Network Security Solutions
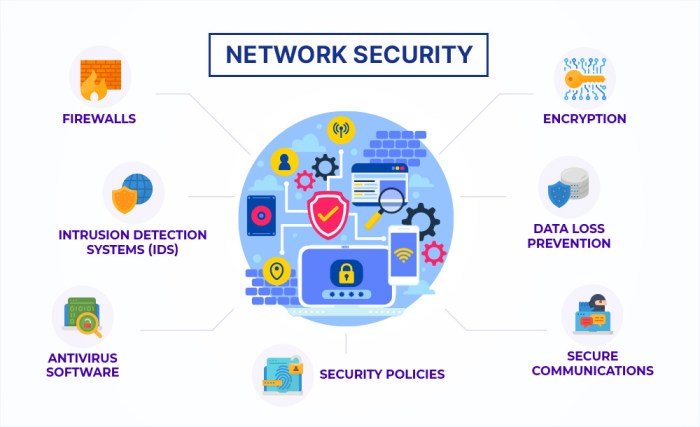
Network security solutions are the technological and procedural safeguards implemented to protect computer networks and data from unauthorized access, use, disclosure, disruption, modification, or destruction. A robust approach goes beyond simply installing software; it requires a multi-layered strategy encompassing various technologies and best practices. This ensures comprehensive protection against the ever-evolving landscape of cyber threats.
Core Components of a Robust Network Security Architecture
A robust network security architecture typically incorporates several key components working in concert. These components are designed to provide defense in depth, meaning multiple layers of security work together to protect the network. A failure in one layer doesn’t necessarily compromise the entire system. These components include firewalls, intrusion detection/prevention systems, virtual private networks (VPNs), antivirus software, data loss prevention (DLP) tools, and robust access control mechanisms.
Each component plays a critical role in maintaining the overall security posture.
Types of Network Security Threats and Vulnerabilities
Network security threats are numerous and constantly evolving. These threats can broadly be categorized into malware (viruses, worms, Trojans), phishing attacks, denial-of-service (DoS) attacks, man-in-the-middle attacks, SQL injection attacks, and zero-day exploits. Vulnerabilities, on the other hand, are weaknesses in a system’s design, implementation, operation, or internal controls that can be exploited by these threats. Common vulnerabilities include outdated software, weak passwords, unpatched operating systems, and misconfigured network devices.
Understanding both threats and vulnerabilities is crucial for effective security planning.
Examples of Common Network Security Solutions
Various network security solutions address specific threats and vulnerabilities. These solutions are often categorized by their function.Firewalls act as the first line of defense, controlling network traffic based on pre-defined rules. Intrusion detection systems (IDS) and intrusion prevention systems (IPS) monitor network traffic for malicious activity, alerting administrators or automatically blocking threats. VPNs create secure connections over public networks, encrypting data to protect it from eavesdropping.
Antivirus software scans files and systems for malware, removing or quarantining identified threats. Data Loss Prevention (DLP) tools monitor and prevent sensitive data from leaving the network without authorization. Multi-factor authentication (MFA) adds an extra layer of security to access control, requiring multiple forms of verification before granting access.
Comparison of Firewall Types
The following table compares different types of firewalls based on their features, strengths, and weaknesses:
| Type | Features | Strengths | Weaknesses |
|---|---|---|---|
| Packet Filtering Firewall | Examines individual packets based on header information (IP address, port number, protocol). | Simple to implement, relatively inexpensive. | Limited inspection capabilities, vulnerable to sophisticated attacks. |
| Stateful Inspection Firewall | Tracks the state of network connections, allowing only expected return traffic. | Improved security over packet filtering, more effective against some attacks. | Can still be bypassed by sophisticated attacks, requires more processing power. |
| Next-Generation Firewall (NGFW) | Combines traditional firewall functions with advanced features like deep packet inspection, application control, and intrusion prevention. | Comprehensive security, enhanced threat protection, granular control over network traffic. | More complex to manage, can be more expensive. |
Implementing Network Security Solutions

Implementing robust network security requires a strategic and layered approach. A successful implementation goes beyond simply installing software; it involves careful planning, meticulous execution, and ongoing maintenance. This section details the process of building and maintaining a secure network environment.
A multi-layered security approach, often referred to as defense in depth, is crucial for mitigating risk. This strategy employs multiple security controls at different levels of the network infrastructure, ensuring that if one layer fails, others are in place to prevent a breach. This redundancy significantly reduces the likelihood of a successful attack.
Multi-Layered Security Approach
Implementing a multi-layered security approach involves a phased deployment. The first layer typically focuses on perimeter security, utilizing firewalls, intrusion detection/prevention systems (IDS/IPS), and virtual private networks (VPNs) to control access to the network. The second layer concentrates on internal network security, including segmentation, access controls (role-based access control or RBAC), and data loss prevention (DLP) tools. The third layer, focused on endpoint security, protects individual devices (computers, servers, mobile devices) with antivirus software, endpoint detection and response (EDR) solutions, and strong password policies.
Finally, regular security audits and penetration testing validate the effectiveness of the layered approach and identify vulnerabilities.
Network Security Plan for a Small Business
A small business network security plan should prioritize simplicity and effectiveness. Key components include a robust firewall to control network access, antivirus software on all devices, strong password policies enforced through a centralized management system, regular software updates to patch vulnerabilities, and employee security awareness training. Integration involves configuring the firewall to work with the antivirus software and implementing centralized log management for monitoring and incident response.
Consider cloud-based security solutions to manage backups and security updates more efficiently. For example, a small business might use a cloud-based firewall service, integrate it with their antivirus software via a centralized management console, and schedule regular backups to a secure cloud storage provider.
Securing Network Devices
Securing network devices (routers, switches, etc.) involves several best practices. These devices are often overlooked security vulnerabilities. Regular firmware updates are paramount to patch known security flaws. Strong, unique passwords should be used for all administrative accounts, and access to these devices should be restricted using access control lists (ACLs). Regular security audits should be conducted to identify and address misconfigurations.
Furthermore, enabling logging and monitoring capabilities allows for early detection of suspicious activity. For example, enabling SSH access instead of Telnet for remote management enhances security.
Regular Security Audits and Penetration Testing
Regular security audits and penetration testing are essential for identifying vulnerabilities and weaknesses in a network’s security posture. Security audits involve a systematic review of security controls, policies, and procedures to ensure compliance with industry best practices and regulatory requirements. Penetration testing simulates real-world attacks to identify exploitable vulnerabilities. Both audits and penetration testing provide valuable insights for improving the overall security of the network.
The frequency of these activities depends on the organization’s risk tolerance and the sensitivity of its data. For example, a financial institution would conduct these activities more frequently than a small retail business.
Network Security and IT Support
IT support plays a crucial role in maintaining a company’s network security posture. They are the first line of defense against many threats and are responsible for implementing and maintaining security measures, responding to incidents, and educating users about best practices. A strong IT support team is essential for a robust and resilient network security strategy.
The Role of IT Support in Maintaining Network Security
IT support’s responsibilities extend beyond simply troubleshooting technical issues. They are actively involved in the implementation and ongoing maintenance of security protocols, including firewall management, intrusion detection system monitoring, vulnerability scanning, and user access control. They also educate employees on security best practices, such as password management and phishing awareness, and respond to and investigate security incidents. Proactive monitoring and maintenance performed by IT support significantly reduces the likelihood and impact of security breaches.
Common IT Support Challenges Related to Network Security Incidents
Responding to network security incidents presents numerous challenges for IT support teams. These include the rapid identification and containment of threats, the need for swift and effective remediation, and the potential for significant disruption to business operations. Resource constraints, such as limited staffing or inadequate tools, can exacerbate these challenges. Furthermore, the increasing sophistication of cyberattacks necessitates continuous professional development and the adoption of advanced security technologies to effectively mitigate emerging threats.
The lack of clear incident response plans can also lead to delays and inefficiencies during a security breach.
A Step-by-Step Procedure for Handling a Suspected Security Breach
A well-defined incident response plan is crucial for effective handling of suspected security breaches. Here’s a step-by-step procedure:
- Detection and Identification: Identify the potential breach, gather preliminary information, and assess the scope and impact.
- Containment: Isolate affected systems to prevent further damage or data exfiltration. This might involve disconnecting infected machines from the network or blocking malicious traffic.
- Eradication: Remove the threat from affected systems. This may involve deleting malware, patching vulnerabilities, or reinstalling operating systems.
- Recovery: Restore systems and data to their pre-breach state. This often involves using backups and implementing data recovery procedures.
- Post-Incident Activity: Analyze the incident to identify weaknesses in security defenses, implement corrective actions, and document the entire process for future reference. This includes updating security policies and procedures.
Essential Security Tools and Resources Used by IT Support Teams
Effective network security relies on a range of tools and resources. IT support teams utilize these tools daily to maintain a secure network environment.
- Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for malicious activity and can automatically block threats.
- Firewalls: Control network access by filtering incoming and outgoing traffic based on predefined rules.
- Antivirus and Antimalware Software: Detect and remove malware from systems.
- Vulnerability Scanners: Identify security vulnerabilities in software and hardware.
- Security Information and Event Management (SIEM) Systems: Collect and analyze security logs from various sources to detect and respond to security incidents.
- Endpoint Detection and Response (EDR) Solutions: Provide advanced threat detection and response capabilities on individual endpoints (computers, servers, mobile devices).
- Data Loss Prevention (DLP) Tools: Prevent sensitive data from leaving the network unauthorized.
- Security Awareness Training Materials: Educate users about security threats and best practices.
Securing your network is an ongoing process, not a one-time event. By implementing a multi-layered approach, staying informed about emerging threats, and investing in regular security audits and employee training, organizations can significantly reduce their vulnerability to cyberattacks. This guide has provided a foundation for understanding network security solutions; continuous learning and adaptation are crucial in this ever-evolving field.
Remember, a strong security posture is a proactive investment, safeguarding valuable data and ensuring business continuity.
FAQ Resource
What is a firewall and how does it protect my network?
A firewall acts as a barrier between your network and the internet, controlling incoming and outgoing network traffic based on pre-defined rules. It filters malicious traffic, preventing unauthorized access and protecting against various threats.
What is phishing and how can I protect myself from it?
Phishing is a cyberattack where malicious actors attempt to trick you into revealing sensitive information (passwords, credit card details) by disguising themselves as a trustworthy entity. Be wary of suspicious emails, links, and requests for personal information. Verify the authenticity of communications before responding.
How often should I update my network security software?
Regular updates are crucial. Software vendors constantly release patches to address vulnerabilities. Aim for automatic updates whenever possible or schedule regular manual updates according to the vendor’s recommendations.
What is multi-factor authentication (MFA) and why is it important?
MFA adds an extra layer of security by requiring multiple forms of authentication (e.g., password and a code from your phone) to access accounts. This significantly reduces the risk of unauthorized access even if your password is compromised.





